How are People able to Intercept your Communications on the Internet?
Protocols are sets of rules that govern how devices on a network communicate with each other. These rules can include anything from how data is formatted before being sent, to the order in which messages are sent and received. In the world of information technology, there are protocols for just about everything, from email to blockchain applications and DNS servers.
Some of the most popular protocols include:
-IP (Internet Protocol): governs how packets of data are sent and received over the internet.
-HTTP (Hypertext Transfer Protocol): enables communication between web servers and clients (i.e. your web browser).
-FTP (File Transfer Protocol): used for transferring files between computers.
Why are protocols important?
Information technology protocols are important because they help to ensure that all computers in a network are speaking the same language. This is necessary so that information can be shared easily and without interruption.
Additionally, some protocols can help to secure a network by limiting access to certain users or devices. And, finally, protocols can help to optimize the flow of data through a network, thus improving performance.
There are many different network protocols, but they all perform one of three primary actions:
- Communication
- Network management
- Security
What is HTTPS?
HTTP (Hypertext Transfer Protocol) is the underlying protocol used by the World Wide Web. HTTP defines how messages are sent between a web browser and a web server, including the format of the messages and the way in which information is transferred.
HTTP is a request-response protocol. A web browser makes a request for a web page, and the web server responds with the requested page. The format of the request and response is defined by HTTP.
HTTP uses TCP (Transmission Control Protocol) as its transport layer protocol. TCP ensures that messages are delivered reliably and in order.
HTTPS (HTTP Secure) is a communications protocol that provides secure communication on the internet. It uses TLS (Transport Layer Security) to encrypt all data between the server and the client, ensuring that no third party can intercept or read any communication. This makes it an ideal protocol for online banking, shopping, and other activities where privacy and security are important.
HTTPS is widely used on websites that require authentication, such as bank websites and online stores. It is also being increasingly used for email encryption, to protect against spying.
What is the difference between HTTP and HTTPS?
HTTP and HTTPS are two different protocols for communication on the internet. They are both equally important, but there are some key differences between them.
HTTP, or HyperText Transfer Protocol, is the standard protocol for communication on the web. It is the foundation upon which data is transmitted between web browsers and web servers. HTTPS, or HyperText Transfer Protocol Secure, is an extension of HTTP that adds an extra layer of security by encrypting data before it is sent over the internet. This helps to protect sensitive information from being intercepted by third parties.
But, how are people able to intercept your communications on the Internet?
There are a couple of ways that people can intercept your communication on the internet. One way is if they are on the same network as you, and use freely available tools like Wireshark.
This means that they can see all of the traffic going in and out of your device.
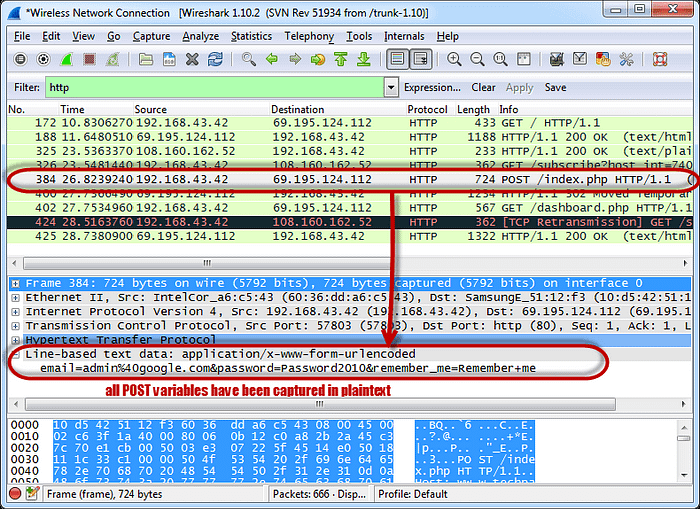
Wireshark is a network protocol analyzer, and is used for network troubleshooting, analysis, development, and security auditing. Once it’s installed, open up Wireshark and select the network interface you want to capture packets from. A network packet is a unit of data that is sent across a computer network. It can be thought of as the basic unit of information in computer networking.
A packet includes both the header and the payload. The header includes information such as the source and destination addresses, as well as other control information. The payload is the actual data that is being sent.
Wireshark will display all of the packets that pass through the selected network interface. In the picture above, the analysis of the packet shows the email and the password “Password2010”.
What can I do to protect myself?
It’s possible that someone who was in your vicinity (say, in the same room or office) when you were using your laptop and connected to the WiFi network could see your traffic.
First, make sure you always use HTTPS when you need to enter credentials or payment details on a website. This will help address some security concerns.
If you’re concerned about others being able to see your traffic, you can use a virtual private network (VPN) which will encrypt all of your data so that nobody else can see it.
VPN IS NOT A MAGICAL ALL IN ONE SECURITY SOLUTION ! :D
A VPN, or Virtual Private Network, is a tool that allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-locked content, such as games or streaming services that are only available in certain parts of the world. They can also be used to improve your privacy and security online by tunneling your traffic through a server in another country, making it difficult for anyone to track or monitor your activity.
There are many different types of VPNs out there, and choosing the right one depends on your needs. Some common features to look for include support for multiple devices, data encryption, speed and reliability, amongst others.
VPNs are often thought of as being a more secure way to browse the internet, and while they can offer some security benefits, it’s important to remember that they’re not perfect.
Follow Magda on Twitter: https://twitter.com/m49D4ch3lly

By Magda Chelly
Chief Security Officer | TEDx Speaker | Author & Keynote Speaker | IFSEC Global Top 20 Cybersecurity Influencer | Entrepreneur | PhD, S-CISO, CISSP, Cert SCI (General Insurance)
Find out on magda-on-cyber.com
Awards
- The IFSEC Global influencers in security and fire 2021
- Top Women in Security Asean Region 2021 Awards https://www.asiapacificsecuritymagazine.com/winners-and-judges-of-the-top-women-in-security-asean-region-2021-awards/
Follow Magda on her Social Media Accounts:
- LinkedIn: https://www.linkedin.com/in/m49d4ch3lly
- Twitter: https://twitter.com/m49D4ch3lly
- Facebook: https://www.facebook.com/m49d4ch3ly
- Instagram: https://www.instagram.com/m49d4ch3lly
